People frequently ask How to protect my accounts and my email address from hackers before discussing two-factor authentication, especially since smartphones retain all passwords from emails, social networking sites, etc., as well as record all personal and financial information, which calls for protecting it well.
The password used on phones and other electronic devices is typically theft-prone; it is not thought to be strong enough to protect data because there are numerous ways for certain hackers to access it, regardless of how challenging those ways may be. By enabling two-factor authentication, you can easily increase the security of your accounts. You should also avoid using the same password across all of your accounts because doing so could make it quicker and easier for hackers to gain access to them.
A vital first line of protection against hackers is taking the necessary precautions to keep your password secure. However, using two-factor authentication, also known as multi-factor authentication or two-step verification, is the best option to safeguard your accounts.
What is two-factor authentication for data protection?
The American website FTC explains that two-factor authentication is a specific type of multi-factor authentication that improves access security by requiring two ways, commonly known as authentication factors, for verifying your identity. These elements may include things you already have, like a smartphone app to accept authentication requests, as well as things you know, such as your account and password.
Your logins are protected by 2FA, which guards against fraud, social engineering, and password cyberattacks as well as weak or stolen credentials being used by attackers.
It is considerably safer to use factor authentication, which is like having two locks on your door. Without a second credential or authentication factor, a hacker will not be able to access into your account even if they have your login and password.
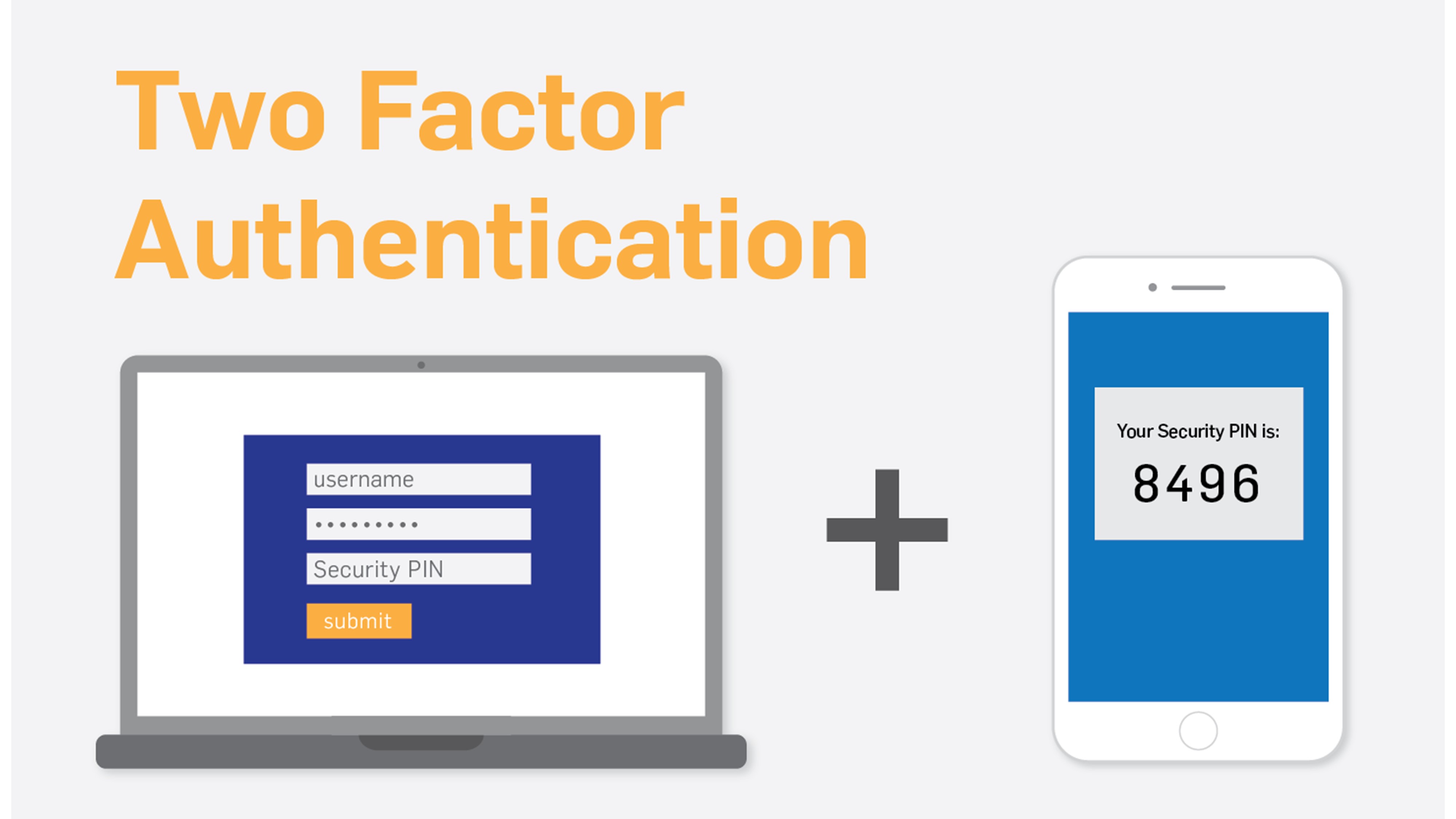
Send a code via text message or email
You can get a verification password with this method of authentication via text message or email. These codes, which typically have six numbers but can be longer, are only valid for one login and automatically expire.
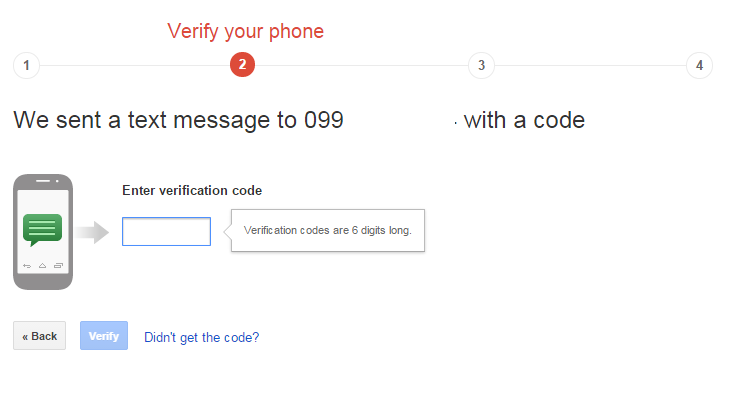
Because it simply needs a phone that can receive text messages, the popular and straightforward technique of receiving the passcode through text message has some drawbacks. Before you know someone has stolen your phone number, hackers can take control of it through a SIM swap assault and send text messages to it, including those containing verification codes.
Use two-factor authentication and a strong password on your email account if you receive a verification code by email. In order to steal your one-time passcode, it will be more difficult for someone to break into your email account.
Even if receiving a verification passcode by text or email is the account’s only available option, it’s still preferable than nothing.
Authentication application for data protection
Some accounts allow you to use the authentication software on your phone or tablet to confirm that you are attempting to log into it, according to the American ” duo ” website. “Google Authenticator” and “Microsoft Authenticator” are two of these programs.
Typically, these apps produce a verification passcode, similar to one you could receive by text message or email. However, utilizing the program is safer since, unlike SIM cards and email, the passcode is not susceptible to assault.
Every time someone tries to get into your account, these apps also provide you the choice to receive a notification right away on your phone or tablet. The notification could include information regarding the sign-in attempt, such as the account being attempted, the user’s location, and the device they are utilizing.
Privacy and security key
You use security keys, which are real things, as a second authentication element. They come in a variety of sizes and forms. You can get one from your employer or purchase one for personal use. Encryption is used with security keys to ensure that the key is associated with your account.
Some of them plug into a USB port. When held close, people can connect to your device through near field communication (NFC). Because they do not employ credentials that can be stolen by hackers, security keys are the most secure kind of two-factor authentication.

Passkeys feature from Google
Google’s PassKeys offer an alternative to passwords for logging into programs and websites, and they stand out for being simpler and more secure than traditional passwords. Using PassKeys eliminates the need to think of a password, save it, or keep it in password management software, as well as limiting access to accounts. due to the use of common, simple passwords.
PassKeys let users enter into apps and websites using their device’s biometric features, such as their fingerprint, face, or screen lock code, rather than passwords.
According to Google, passkeys, as opposed to passwords, are more resistant to phishing and online scams and are more secure than SMS verification.
:quality(90)/cloudfront-us-east-1.images.arcpublishing.com/sdpnoticias/HM4UNWN3SZH3ZHW4FEPZMLVMRU.jpg)
conclusion
In conclusion, protecting your accounts and email addresses from hackers is essential in a world that is becoming more and more digital and interconnected. You may greatly lower the danger of unauthorized access to your sensitive information by putting in place a mix of robust security measures and proactive procedures. For each of your accounts, start by making complex, one-of-a-kind passwords, and enable two-factor authentication whenever it is practical. Update your passwords frequently, and watch out for phishing scams and unusual communications.
FAQs
1. Why is it important to protect accounts and email address from hackers?
- Protecting your accounts and email address is crucial to avoiding identity theft, unauthorized access, and possible misuse of your personal data.
2. What are some common methods hackers use to gain access to accounts and email addresses?
- To compromise accounts and email addresses, hackers often use techniques including phishing, malware, password guessing, and brute force attacks.
3. How can I create strong and secure passwords?
- Use a mix of capital and lowercase letters, numbers, and symbols to create complicated passwords. Useless information like birthdays or frequent nouns should be avoided.
4. Is two-factor authentication necessary for all my accounts?
- It is strongly advised for all accounts that support it to enable 2FA. By demanding a second verification step, generally a code texted to your mobile device, it offers an extra degree of protection.
5. What should I do if I suspect a phishing email or a suspicious login attempt?
- Do not open any links or download any attachments if you receive a suspicious email. Both remove and report it. If you notice any unusual login attempts, reset your password right away and turn on 2FA if it isn’t already.
6. How often should I update my passwords?
- Regular password updates are advised, ideally every few months. In the event that your passwords are stolen, this helps protect your accounts.


